Forensic research into an FX29 Compromise
March 14, 2013Recently I was tasked with looking into a server that appeared to have been compromised. Various symptoms included load average of 18+, and processes such as “perl scanz.txt” showing up all over the place.
Where to start?
The biggest difficulty was figuring out what exactly was compromised. The server had dozens of virtualhosts on it and they all logged independantly. The backdoor seemed to keep changing process names, but after several tries, a well timed “updatedb, ps waux, locate Suss process” dropped me in the correct directory. There we found the famous fx.php, indicating the presence of the Fx29 worm
Then it got silly
Some basic discussion on Fx29 can be found on Andrew Martin’s Blog. One of the things you’ll find discussed there is a reference to the ability of the application to log back to the attacker, using a special field in the source code. In our edition, we found this line: $log_email = ”rio.rizaldy@yahoo.com”; Which is consistent with your average Fx29 hacker using a remotely anonymous email. Until said idiot created a Facebook account linked to that address:
Congratulations Rio Rizaldy. It’s been a long time since someone this stupid decided to take over the Internet. I now congratulate the intelligence of someone who adds a random Facebook friend, with the “personal message” of lolpants, and allows me to make stupid comments on your page for over a week.
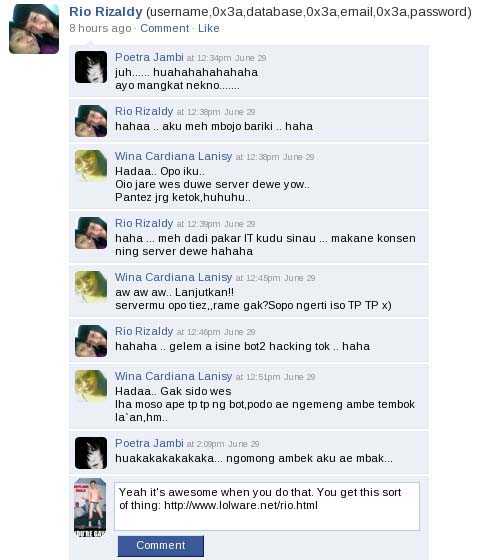
As much as I don’t speak Indonesian, what we’re looking at here is a status update featuring a refernce to the compromise in question, references to “bot” and “hacking”, and my second reply showing him this website.
Update!
It would appear that Rio has deleted himself from Facebook. Let’s hope all his friends don’t take it personally.